Open Source Security
Proposals for securing projects through a fund
Dr. Thomas Fricke
On behalf of the Prototype Fund
Version: 0.9, 8 September 2021
License: Creative Commons License CC BY-SA 3.0 EN
Authorized Deepl translated version
Summary for the decision
Open source is an important economic factor and contributes to billions in value creation per year. There are numerous projects that are used in security-relevant areas. These initiatives need support in the area of process automation and modern, secure procedures.
The communities are very security-conscious and deliver secure open source packages at a stable level. However, more elaborate methods of securing software processes are not standard because there are not enough human resources available in the projects. Sometimes communities work at the edge of their capabilities. In order to implement secured processes, support by a fund in the range of 15-30 million € / year is suggested. The goal must be a largely automatic analysis and installation of the software. On the other hand, there are risks for potential damages in the high billion range.
The proposed projects are important for industrial application from the field of clouds, Gaia-X, machine learning and the further development of deployment. In addition, there are real laboratories for future security technologies in the energy and industrial sectors to raise modern security paradigms to the standard.
Responsible disclosure is suggested for dealing with security vulnerabilities. The fund should be managed by technically experienced persons who are recognized in the community in order to achieve acceptance.
The document addresses what the author considers to be important examples. It is not a representative analysis and is based on personal experience over the last decades. There are many more projects that deserve mention.
Economic importance of Open Source
The economic impact of open source is 65-95 billion euros in 2018 , according to the results of the Open Source Impact Study1 . The use runs through all areas of economic life, from private mobile phones2 , routers3 , televisions4 , vehicles5 , telecommunications infrastructure6 , to industrial plants with thousands of pages7 of software inventory list in the SBOM8 . The importance goes so far that specialized open source products are co-developed by Bosch and Siemens , among others , for the automated collection of all components , which allow the automatic creation of SBOMs from the source code9. In addition, Bosch, BMW, Daimler and Siemens have their own groups working on the standardization of open source compliance as part of the open chain project on ISO 5230. The 10share of software in value creation in cars is estimated to reach 60% in just a few years11.
For the use in public authorities and the further development of open source by the public sector, the fundamental questions have already been clarified.12 Many of the aspects discussed also apply to the economy.
Security of Open Source vs Closed Source products
The assumption that only enough eyes need to look at the code to bring all bugs to the surface, also called Linus's law13[, is used to argue for FOSS in the security debate. However, it does not say how many eyes, nor how often they should look at the code.]
In contrast, closed source does not mean that the binary code cannot be read. There are appropriate tools14 and software engineers experienced15 in reverse engineering who, with their help, are also able to read binary code; even chips16 can be analyzed with the appropriate effort. If these systems contain a global key17, for example, this knowledge spreads very quickly on the Internet and entire groups of systems are discredited at a stroke and are massively attacked after a very short time18. The security holes become known at the latest with the patch and the attacks begin within a day19[.]
All this shows that security by obscurity20 is not a strategy to secure systems and only increases the effort to discredit a closed system. This has been known in principle since the 19th century21. Also the totally inadequate update process in medical telematics components22shows that under such circumstances the number and criticality of known security vulnerabilities for a device can have serious consequences over time.
Manufacturer support for durable assets
For components with already expired or expiring manufacturer support
the manufacturer no longer informs about new vulnerabilities, even if they become known (so-called "end-of-life" components). Therefore, it is essential for operators to monitor whether manufacturer support is still offered for all components used.
The security status of the component is unknown without support and a "worst case assumption" is required. The operator now has the responsibility to take measures so that security vulnerabilities in the components cannot be exploited. For example, this can be enabled by access restrictions with network segmentation or additional authorization and authentication features in jump hosts. Further measures are described in the BSI Basic Protection Compendium, among others 23.
The problem of end-of-life components can be circumvented in the field of open source. For example, in order to continue operating classic operating systems such as VAX/VMS or Solaris, OpenVMS24and OpenSolaris have 25been supplied with upgrades and new features by a community for years.
Cloud providers are showing a trend here, as they have been relying primarily on open source for security-relevant components such as operating systems, libraries, cloud26, network components 27and also standard hardware for 28some time. This achieves independence from the underlying hardware and the manufacturer.
The Python example
The example of Python can be used to discuss very well which security requirements are placed on a community software and how security vulnerabilities affect it. Python is a programming language that covers all fields from microcontrollers29to high performance computing. 30As of August 2021, Python has moved up to #2 in the TIOBE Index31, just behind C and ahead of Java and C++. According to the IEEE's assessment, Python has been ranked #1 programming languages in the engineering field for five years 32. This is remarkable because Python emerged from an open source community and not from a corporate project, but like C++ from a university study33. Python still has a non-proprietary community, unlike Java(Oracle, Red Hat, IBM), C++, DotNet (Microsoft), Go (Google), Rust (Mozilla) or NodeJS (NPM). A comprehensive analysis is already available for Java 34.
Python in Critical Infrastructure
Python is the basis for most machine learning frameworks35 and is used extensively in critical infrastructures, e.g. to predict energy consumption and price at the Leipzig Energy Exchange, but also to plan power grids in the network of the German Transmission System Operators and the European Transmission System Operators36 37.
Based on the results of these predictions, transactions on the Leipzig Energy Exchange or circuits in the high-voltage grid above 110kV have been carried out manually up to now, and later also automatically. The effects of these calculations therefore have indirect and in the future also direct effects not only on electricity trading but also on operational technology38, i.e. industrial control systems, and are thus considered critical infrastructures in the 39sense of BSI and BBK 40. The author is not aware of any systems whose failure would have more far-reaching consequences. A failure would have a direct impact on the economy and security in Germany and Europe.
Python Releases
Community support for releases is three years, with the exception of the last release of Python 2, version 2.7 with 10 years41 to facilitate the move to Python 3. The migration was extended again and again because the user community could not complete the migration.
Python Security
The Python ecosystem affects not only the programming language itself, but also the central library repository, the Python Package Index PyPi42 with hundreds of thousands of packages and millions of releases. Hidden in that set of packages is malware. The attackers try to exploit typos in the package name to initiate an installation. This method, called typosquatting43is now being fended off 44. This can be used to initiate all kinds of attacks, e.g. data theft 45or further compromise of even critical systems.
Existing security projects
The problem is not unrecognized. Already within the Horizon 2020 project46, there were efforts to investigate licensing and security compliance as a Fasten 2020 initiative47. The initiative has so far not had any profound success, mainly because the breadth of the questions, fluctuations in the project and lack of anchoring in the community have not led to sustainability. Also, in the author's opinion, typosquatting cannot be detected with existing compliance patterns. The Google Insights48 project has addressed Python but has not yet implemented it. In this case, it is only possible to identify relevant packages, automatically scan them with all their dependencies and qualify them as checked. In applications, packages secured in this way no longer need to be audited separately.
The Python Security Project49 has fallen asleep because it was not continued after the end of Python 2.7.
An audit process that qualifies and signs individual projects50 and a PyPi mirror51 with audited packages are obvious ways to distribute only relatively safe packages. The Python community itself has 52made a proposal for a curated index, which is logically very similar to the idea of a mirror. A curated index is like a virtual mirror.
The bottleneck is clearly the low staffing, only one person works part-time paid for PyPi53 . Implementing these ideas would easily require several full-time positions for development and administration.
Embedding in other projects
There are a number of similar projects into which these activities can be integrated. These include the Linux Foundation's54 The Update Framework project 55, which aims to make update systems secure. A Python version, updaterpy already exists 56. Other projects, such as securing deployment pipelines through SigStore 57, integration with the Open Security Foundation 58and its project
ScoreCards59 are highly recommended. With the appropriate equipment, newer projects such as Google Insights could also be supported.
Bringing it together under one organization that supports open source security along with the community is urgent. The contradiction between economic value and resources needed by the community is grotesque. On the side of value creation we have billions of benefits, with corresponding risk in case of failure, for a damage in the European Critical Infrastructure without further ado also a trillion risk ($10\ ^{12}$€), on the other hand a community that organizes the project itself and has created the Python Foundation, an organization that not only drives the development of the programming language into one of the most important languages for all kinds of applications, but also supports conferences with a budget in the low millions60, compared to the revenue Firefox gets for selling search to Google61.
On the other hand, security is practically done on the side and or in the spare time. Funding in such as through the Core Infrastructure Initiative62 is urgently needed. Before the Heartbleed63 security breach, OpenSSL64 , the library responsible for encrypting most Internet connections through TLS65, had a funding of a paltry $2,000 per year; afterwards, through industry donations, among other things, the amount jumped to a few $100,000 per year. The Core Infrastructure Initiative (CII)66, a sub-organization of the Linux Foundation, is funding two full-time positions.
Containers and Kubernetes
The container ecosystem has 67spawned an entire ecosystem since the proliferation of Docker in 201368 as a simplification of Linux Containers. Orchestration, i.e. managing the interplay of many containers connecting distributed microservices69cloud native applications, is 70now almost exclusively implemented with Kubernetes.71
Based on its own container system "Borg", Google decided in 201472 to make Kubernetes available as open source. All cloud providers and well-known software companies offer products in the Kubernetes ecosystem, which are certified73 by the Cloud Native Computing Foundation CNCF74. The landscape75 includes nearly a thousand projects. Behind the startups in this field venture capital investment in the range of nearly 20 billion. Kubernetes taps from the use of a lightweight variant K3S in IoT76to the use in the military 77and in the cloud 78.
There are now cluster management systems, i.e. systems that manage clusters themselves again, that 79can manage millions of clusters. Numerous German cloud providers have taken up the deployment of Kubernetes in their data centers as a business model and offer a version managed by them.80
Likewise, the 5G mobile network is secured from the core to the cell towers with Kubernetes and containers81.
Gaia-X
The main idea of Gaia-X82 is to provide federated services83 in an ecosystem. The Sovereign Cloud Stack84 , a description of the necessary components and interfaces through an integration of Kubernetes in Openstack85 is an exemplary reference architecture. It includes existing and future components of standardized sovereign cloud and container infrastructures that complement each other. The goal is to define, implement, and operate a fully open, federated, and interoperable platform.
What's notable about this is that the Kubernetes components in it are mandatory, but the implementations on Open Stack are optional 86. All components are under open source licenses, Open Stack is largely 87implemented in Python and would also directly benefit from securing the Python ecosystem.
Security in the Container Ecosystem
Due to rapid growth, complexity has grown to the point where the majority of users are already noticing security issues88. The technical problems range from containers with malware, wrong decisions in the architecture of Kubernetes and misconfigurations in the application. Of particular concern is that many gaps often remain unaddressed years later. DockerHub89is the most comprehensive and important registry 90for containers. The insecurities that were complained about for images in 2015 91are still present in 202092:
Almost 51% of the images had critical vulnerabilities that could be exploited and 68% of the images were vulnerable to varying degrees. 0.16% or 6432 of the images analyzed contained malware*.*
The cloud providers and manufacturers are shifting the responsibility to the operators and developers, who are completely overwhelmed with the task of securing in the first place.
There is a lack of sustainable, effective and applicable processes that deal with the detection and permanent elimination of security-relevant difficulties. Red Hat alone has a commercial offering with a container catalog93that keeps important basic containers up to date and evaluates their security with a health index based on American school grades94. Productive use requires a Red Hat subscription.
Plans for similar offerings for other distributions are not known. It 95Debian-based distributions and Alpine96. Debian-based systems, including Ubuntu, are the most common with almost 50%97. Alpine containers are very widely used because they are optimized for size and are much smaller, sometimes a factor of 3, than other container distributions98 and thus save resources in the cloud environment and can be deployed much faster. Typical automated processes in deployment pipelines involve thousands of images and, given the same resources, container processes built on Alpine are correspondingly faster. Alpine has a strict security policy that replaces even established tools and libraries to keep the attack surface as small as possible99. For this reason, Alpine is also a very good candidate for reproducible builds100.
Kubernetes security
Due to the complexity of Kubernetes, it is virtually impossible to securely set up and operate a Kubernetes cluster with reasonable effort101. Investigations with Aqua Security's Kubebench, which is based on the 102CIS standard103, almost always find security vulnerabilities that allow an attacker to take over a cluster104. With appropriate Kubernetes knowledge, it is even possible to build a parasitic control plane controlled by the attacker that is not detected during normal operation 105. The security depth, defined as the number of flaws that must coincide to allow a full compromise, is four.
-
Error in the application106,
-
Access to the SecurityToken 107
-
Local installation possibility,
it is enough to be able to write into a temporary directory 108 -
Ununderstood role-based access control 109
Point 1 is a common error in applications110, point 2 is the default ! setting, point 3 is also almost always met, even in "secure" containers. Point 4 needs a common misconfiguration, often described on the Internet as part of an installation guide. These factors meet very often in practice.
Kubernetes offers numerous options for operating containers in a secure and hardened manner111. Secure basic configuration at the container level through access controls112 , network policies 113, or zero trust in the form of service meshes114 are already implemented in the form of open source projects ready for use. Unfortunately, the default setting is also insecure here115, although a secure setting is easily possible116. In order to master the further increased complexity, automated security checks are urgently needed, e.g. as an extension or addition to Kubebench (see above). Custom resources117are part of the extension options for Kubernetes, but unfortunately also susceptible to misconfiguration 118.
Side channel attacks
Another problem for the shared use of hardware resources are side-channel attacks on the CPU cache119. This attack is generally threatening to clouds and can also be exploited in classic virtualized systems . The major cloud providers use internal undisclosed customizations to prevent these attacks120 , detection is actually not difficult121 . Previous defensive measures include disabling hyperthreading, which results in a loss of performance, or patches that only close the known gaps. However, new variants are discovered again and again, which cannot be patched with known methods122.
The right place to monitor processes is a dedicated control group for cache misses123 and integration with Kubernetes124 . For this, a corresponding Cgroup module would have to be written and brought into the Linux kernel125.
Key Libraries
Cryptographic key libraries are important for securing the Internet transport layer126especially OpenSSL 127, but the other implementations like GNU TLS, LibreSSL or WolfSSL are also common128.
Implementation errors
Despite its inclusion in the Open Source Security Foundation's program (see above), OpenSSL is often the victim of vulnerabilities129, currently another vulnerability that arose from a lack of understanding of memory management130. It is completely unacceptable that such vulnerabilities are still present in widely used libraries that have been in use for years.
Crypto library updates
The lifetime of cryptographic procedures is in the range of a few years. For no procedure can the BSI currently recommend use for more than five years131. This means that an algorithm that is discredited must be replaced. To date, there are no generally valid processes for this. While the transport layer only needs to be secured in the short term, signature processes are also based on cryptographic processes with a life cycle of several years. This is a problem for IoT in industrial plants in particular, but also for buildings.
The reason for this is on the one hand the long service life of industrial plants, which can be used contractually for up to 30 years, but in some cases are also in operation for 50 years. If the software is integrated into "smart" buildings in the future, the issue of safeguarding may also extend to buildings and their service life132.
Hashlists
The entire range of chained hashlists and blockchain133 depends on the strength of the hash algorithms used. In all these cases, the integrity of the signature must also be ensured when a crypto algorithm is broken. This has happened several times for hash algorithms, most recently collisions have become easy in SHA1134, so now at least SHA2 must be used. After finding a theoretical weakness, it took about a decade to finally make SHA1 unusable.
Asymmetric encryption
Similarly, asymmetric, public-private key, encryption and signature methods135 . The basic assumption that it is mathematically hard to factorize the product of two prime numbers cannot be proven or disproven at present136. Asymmetric encryption is used to replace a symmetric key to speed up for
For the theoretical use of quantum computers, there is already137 a procedure with the Shore algorithm that 138can break asymmetric keys of any length. Because asymmetric keys are the basis of secure communication, in this case the entire encryption of the Internet would be broken. Only the difficulties of building a working quantum computer that implements the Shore algorithm save us from the Quantum Cryptocalypse139. When and if quantum computers will ever be usable is difficult to predict. The EU digital strategy expects a first European quantum computer in 2023 140. It is to be expected that the mass proliferation of quantum computers will also severely shake all crypto methods 141.
Because quantum computers are not universal computers, there have been efforts for several years to 142advance the development of post quantum cryptography. In the meantime, there are many candidates that have been cryptographically investigated and can be rolled out. In most cases they are not slower than the known algorithms, but some of them need much more memory, so that they can only be used in the next generations of smart cards143.
Therefore, it seems important to secure crypto processes, both with regard to existing security gaps as well as to threatening fundamental cuts by quantum computers or missing mathematical proofs for the security of the processes.
Common ground
What all these problems have in common is that they can be solved well with updates. Given the urgency of the problems, it is essential to detect, fix and patch security vulnerabilities, i.e. install a secure version as soon as possible.
This can only be achieved if this process can be automated as far as possible. Static analysis methods are standard144. Google has been looking for security vulnerabilities in C, C++ and Java Virtual Machine based languages for a long time145using fuzzing 146, a method that checks source code by random input and 147is already used in Germany by Bosch, Telekom, Continental and Deutsche Börse 148. The wolfSSL library was checked for common errors149. The method uses a lot of unused computing power. An academic project like Angr 150, which analyzes the control flow more effectively, has had some spectacular successes, but is hardly used.
Secure deployment pipelines
Continuous Integration / Continuous Deployment is the process of continuously assembling components into an application151. It consists of several steps, from checking in the source code to rolling it out in production.
This way of rolling out new software under the keywords Continuous Integration152and Continuous Delivery 153or Continuous Deployment 154has become standard in many modern system environments.
A simple deployment pipeline with elementary security checks is shown in the following picture from the commit of the source code to the rollout into production, i.e. the installation on the target platform.
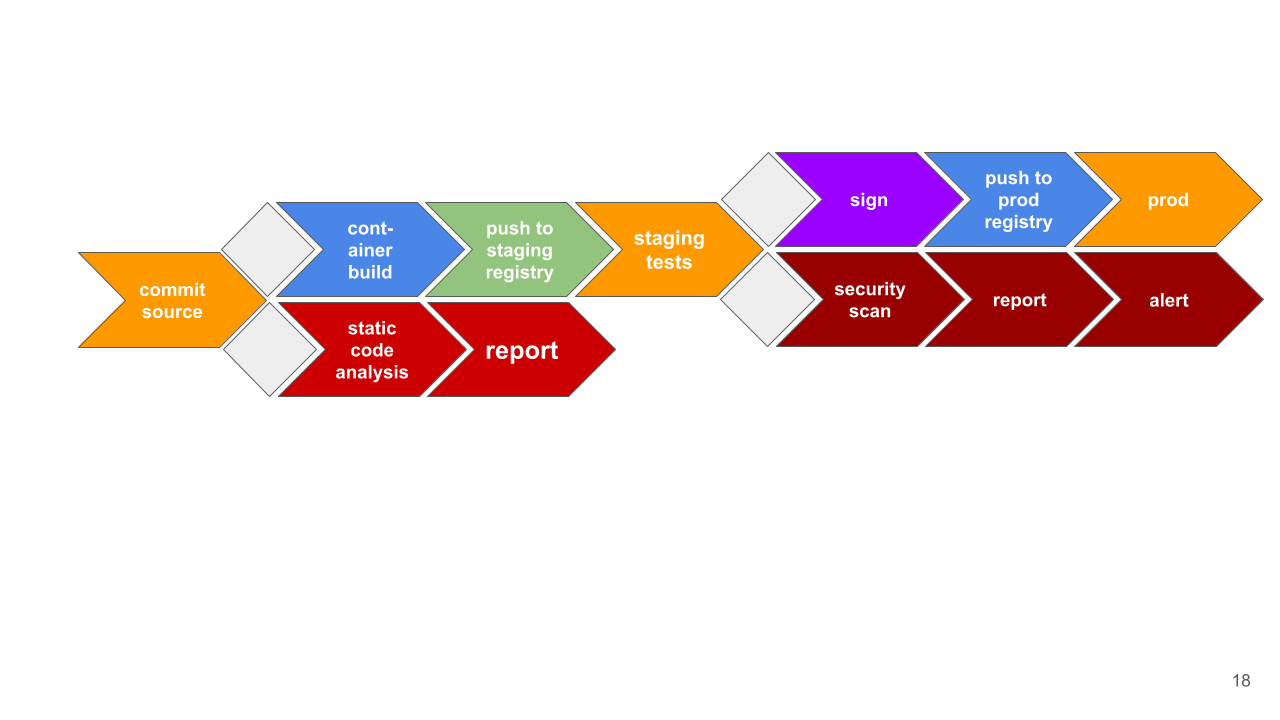
More complex pipelines are easily possible by integrating more tests. For small changes, the pipeline can easily be run through completely in 20 minutes, from commit of the source code to deployment in production155. The security relevant steps are highlighted in red and can run asynchronously, e.g. overnight. A more complex example with separation of the environments can be found at Gitlab 156.
Importantly, the deployment pipeline is the software implementation of a DevSecOps157 process, not simply a tool to be deployed158. A full description of this process has been produced by the Cloud Native Computing Foundation in conjunction with the US Department of Defense.159
This is a significant change that affects not only technology but all processes including the organizational structure itself, also referred to160 as shift-left. The author estimates that implementing these processes in an established organization will take at least five years. The US National Institute of Standards stated this back in 2017 with regard to containers: tailor organizational operating culture and technical processes to enable the new way of developing, operating, and supporting applications in containers 161. There are immediate implications for the operational organization from the technical requirement. Since organizations generally resist change passively at first, this change process must be actively managed.
Efforts for the operation of build pipelines
Compared to the classical work in software development, the use of build pipelines represents a transition from code development to software engineering. The playful motivation of many open source developers is partly opposed by the strict requirements of software engineering. The integration into an automated environment with static code analysis and fuzzing means a change in the way of working, and not to be underestimated effort for the evaluation of the analysis results162. The transformation is not trivial for established projects and very difficult to accomplish without support163.
The example of the established project GnuPG should explain this. The business model has produced G10 Code164, a company that takes care of further development and support. Support and service contracts make GPG usable for classified documents165 for customers from security authorities. The existing developers can also support this model well. However, there is a lack of resources for the maintenance of documentation, automatic code analysis, fuzzing of the code base, setting up deployment processes and further development. External audits take place regularly, but the incorporation of the results means a high additional effort in each case.
The GnuPG association166 is well funded, but lacks resources for community management and external representation. In addition, the aging of the community is also a problem here167.
An initial estimate shows that five to ten full-time positions would be useful here.
Supply Chain Attacks
All packages discussed here are part of the supply chain, which itself is a prime target of attacks 168. 169. Remedies by signing the single steps in the pipeline like by Sigstore 170or the pipeline itself including auditing will become standard in the near future171 . Especially safety-critical code must be built from source code in trustworthy environments, ideally as a reproducible build, see above. Projects cannot afford this software engineering effort on a permanent basis as a part-time job.
Summary and measures
The establishment of an open source security fund seems urgently needed. On the one hand, there are billions in investments that depend on open source; on the other hand, there are no coherent and sustainable measures to safeguard it. For the usual EU research projects like Fasten 2020, there is funding in the range of a few million over three years. At the end of the project, a project report is produced, but there remains no organization to further develop the results and transfer them to the community. The main good approaches for secure DevSecOps processes have strong ties to the US military and should be complemented by a strong, civilian European initiative.
The fund should identify individual projects, communities, and ecosystems and work with maintainers to analyze vulnerabilities and provide resources to fix them. To do this, the most important components must be found and processes defined with the community that can be supported automatically. These processes should also be implemented and secured together.
For a community like the Python Foundation, this would mean several full-time positions due to the number of packages, accompanied by external expertise such as at least annual audits and the provision of curated subrepositories of PyPi. In addition, there would be an appropriately highly secured deployment pipeline. With project and community management, a higher single-digit million amount would need to be used annually. A sustainable investment is important, projects with a finite time horizon always fizzle out. Cooperation with partners should be sought and coordinated.
Other projects worth supporting
Corresponding projects for other programming languages like Ruby or the ecosystem of Owncloud or Nextcloud172 , video conferencing tools like Jitsi or Big Blue Button173 would certainly lead to similar results, depending on the scope of the components. Another example is data center infrastructure, Software Defined Networks can be run securely on common high end hardware even with open source174. Individual cloud providers force hardware suppliers to Linux based operating systems 175or maintain their own infrastructure components derived from open source software. Support for Open Hardware and Open Infrastructure is also warranted with respect to deployment in the Gaia-X initiative 176. Other ambitious projects such as the Linux Phone 177or a modified Android are 178aimed at the privacy of users, but it must be emphasised that their use also directly benefits the security of the economy.
Remarkable is the high competence that German and European providers have already built up, such as BISDN179 in the high end carrier and network market, Nitrokey180 in the field of encryption or K-9 Mail with email encryption181. K9 Mail has launched a funding call for maintenance. K-9 Mail is essentially the project of a single developer182 asking for a comparatively modest amount of funding, most of which has already been raised by the community. This project, with 600,000 downloads, actually depends on smaller companies, each with a hundred employees using K-9 Mail183. When asked about funding, he can't imagine starting a company with his own staff. He would like to see a simple funding option for small open source, such as is offered in the USA by the Open Collective platform. 184
Rating
The interviews conducted for this analysis show a high level of need for support. The communities very often signal, as in the GnuPG example, that they are well provided for185, but on closer enquiry it becomes apparent that this statement is only true at a low level. The equipment of the projects, like GnuPG, Python or Alpine Linux is only sufficient for a minimal demand. If one asks for professional software development that includes automation, such as deployment pipelines, automatic security analyses, fuzzing or audits, there are deficits in many areas. The community makes up for this with overwhelming personal commitment, but at the price of burnout, which has also arrived in the open source communities. With the proper awareness, the symptoms can even often be observed186.
All community projects signal that they would very much welcome further resources. Selected small projects by individual developers should be funded easily and without much bureaucracy, and it should also be possible to support freelance developers.
Strategic projects
There is also an urgent need to support strategic projects in the cloud area. This also includes edge computing187, which will be a necessity in the future in the area of massively distributed systems, such as in smart energy188 management and real-time industrial control189. Edge computing, for example through K3S190 is a lightweight Kubernetes, comes from cloud computing. In the whole area of cloud orchestration, even BSI is weak 191. Modern security architectures like Zero Trust192 , widespread adoption of multi factor authentication193 , OpenID194 and cheap signature services195 for documents or certificates ACME196 are needed in this area . Initiatives such as the Souvereign Cloud Stack197 are seemingly well equipped via Gaia-X and funded projects, but also cannot fully cover this area. An integration of Chaos Security Engineering198into this architecture is also recommended 199.
Organization of an Open Source Security Fund
It must be the task of the fund to ensure sustainable and sufficient equipment for the supported projects. In addition to development, this includes reasonable automation, audits and professional communication and community management.
It is recommended that criteria be developed to select 10-20 communities, determine maturity and need, and create 5-10 full-time positions in each. More are not to be moved with a fund at the beginning.
In addition, it makes sense to support an equal number of smaller projects with 2-4 full-time positions. Small and very small projects, including individuals, should be given the opportunity to finance and manage themselves transparently with a structure like Open Collective.
The Fund's leadership positions must be filled by recognized members of the community. Just recently, the Chief Software Officer of the US Air Force resigned because the IT experience of the leadership level assigned to him was not sufficient200. It makes sense that the industry working on the projects should also be able to send representatives with the relevant knowledge. Under no circumstances should the projects be regarded as extended workbenches or even be given instructions.
Reallabs
All these technologies are ready for real use and have the highest technology readiness level201, namely 9. It is therefore not a matter of research projects, but of widespread implementation, e.g. in Gaia-X. A federated development model "one for all" together with the members of the Gaia-X Foundation should be able to make the technology, which a single medium-sized provider cannot offer, available to the provider community across the board for all. It is also important here to have flanking support from the BSI, which concretizes and formalizes the requirements.
Dealing with security vulnerabilities
All security vulnerabilities must be published in a Responsible Disclosure202 process. Under no circumstances may security authorities exploit vulnerabilities that have not yet been published. Trading in security vulnerabilities must be strictly prevented, preferably prohibited. All decisions in this regard must be made by the communities themselves, and political influence must be strictly excluded, because otherwise an important part of the security community will no longer be able to cooperate with the program.
The BSI is also not neutral enough203. The trust of the community in politics has been severely damaged by irrational and technically ill-founded decisions204. Open or covert influence would mean the withdrawal of important players from cooperation with the fund.
Internet bug bounties205 are not a good way to create sustainable security. They create a market that competes with the malware market206.
About the author
Dr. Thomas Fricke
1989 Installation of Unix Cluster, first Linux versions
1994 Doctorate in Aachen
1996-2005 Software developer in employment
since 2005 freelance consultant as software and system engineer
2006 various projects in the area of clouds, automation
Kubernetes since 2015
2013 Co-founder of Endocode AG (now Hoverture Deutschland AG), an open source and cloud service provider
2013-2021 Management Board, CTO and Supervisory Board at Endocode
Kubernetes Projects CoreOs, Google, SAP, Red Hat
2019-2020: Member of the Octarine (now VMWare) Technical Advisory Board.
Independent Cloud Security Architect for Kubernetes and OpenShift since 2017
2021 Co-founder of Resility GmBH (Security Chaos Engineering)
Energy and health sectors
Projects in the security sector for the Bundesdruckerei and mail providers
Honorary participation in the IT Planning Council
-
Study about the impact of open source software and hardware on technological independence, competitiveness and innovation in the EU economy | Shaping Europe's digital future, Preliminary summary in German Study: Open Source contributes €95 billion to EU economic power ↩︎
-
Daimler Advances Connected Car Technology through Open Source and Automotive Grade Linux ↩︎
-
Access 4.0, summary in German Access 4.0: Telekom wants own open source technology for fixed network, https://opennetworking.org/wp-content/uploads/2018/12/DT-Access-4.0.pdf ↩︎
-
author's own personal experience ↩︎
-
BOM Bill of Materials - Wikipedia ↩︎
-
Eclipse SW360 - Presentations, FOSSology,
Bitkom Presentation Lessons Learned from Automated License Compliance ↩︎
-
ISO/IEC 5230:2020 - Information technology - OpenChain Specification, OpenChain: Home ↩︎
-
"In five years, software will account for 60 percent of value creation in cars" | KFZ Wirtschaft ↩︎
-
Legal aspects of the use, distribution and further development of open source software ↩︎
-
["given enough eyeballs, all] [bugs]](https://en.wikipedia.org/wiki/Software_bug) [are shallow" according to] [[Linus's law - Wikipedia]{.underline}]](https://en.wikipedia.org/wiki/Linus%27s_law) ↩︎
-
IDA Pro - Hex Rays , NationalSecurityAgency/ghidra: Ghidra is a software reverse engineering (SRE) framework ↩︎
-
Lecture: Understanding millions of gates | Monday | Schedule 36th Chaos Communication Congress ↩︎
-
Multiple Vulnerabilities in Cisco Unified Communications Domain Manager, German Summary Cisco Removes Backdoor from Unified Communications Domain Manager ↩︎
-
Microsoft says Iranian hackers are exploiting the Zerologon vulnerability ↩︎
-
Indications of possible vulnerabilities in medical telematics | c't Magazin ↩︎
-
JSC - Events 2020 - ONLINE -- PRACE training course "High-performance computing with Python". ↩︎
-
Data Mining and AI languages are booming in the TIOBE index ↩︎
-
Python (programming language) , C (programming language), Java (software platform), C++ ↩︎
-
Best Python Libraries for Machine Learning and Deep Learning ↩︎
-
Own projects of the author ↩︎
-
Federal Office for Information Security, Federal Office for Civil Protection and Disaster Assistance ↩︎
-
Python Typosquatting for Fun not Profit [by William Bengtson ↩︎
-
Python Package Index nukes 3,653 malicious libraries uploaded soon after security shortcoming highlighted ↩︎
-
Software downloaded 30,000 times from PyPI ransacked developers' machines ↩︎
-
https://www.fasten-project.eu/ Introducing the FASTEN project ↩︎
-
Introducing the Open Source Insights Project | Google Open ↩︎
-
https://web.archive.org/web/20210506143150/http://www.pythonsecurity.org/ , ebranca/owasp-pysec: OWASP Python Security Project ↩︎
-
PEP 458 -- Secure PyPI downloads with signed repository metadata ↩︎
-
Allow users to curate their own hosted index - Issue #8812 - pypa/warehouse ↩︎
-
Ernest Durban, ee@python.org ↩︎
-
https://github.com/theupdateframework/tuf/tree/v0.11.1/tuf/client#updaterpy ↩︎
-
Mozilla Signs Lucrative 3-Year Google Search Deal for Firefox ↩︎
-
https://en.wikipedia.org/wiki/Core_Infrastructure_Initiative ↩︎
-
There are numerous precursors, history to 2019: A Brief History of Containers: From the 1970s Till Now. ↩︎
-
Microservice Architecture pattern, Microservices - Wikipedia ↩︎
-
Plusserver What is cloud-native? ↩︎
-
With Kubernetes, the US Department of Defense is enabling DevSecOps on F-16s and battleships ↩︎
-
Google Kubernetes Engine clusters can have up to 15,000 nodes ↩︎
-
The first SUSE version of Rancher Kubernetes is on its way ↩︎
-
Ionos Managed Kubernetes Services: Host your K8s cluster, Cloudshift
https://www.cloudshift.de/kubernetes, Netways Managed Kubernetes - Your Container Orchestration Service, OHVCloud https://www.ovhcloud.com/public-cloud/kubernetes
Syseleven https://www.syseleven.de/products-services/kubernetes, Claranet
Simplify Container Management with Managed Kubernetes
Scaleuptech Managed Kubernetes and Platform as a Service with Docker and many others. ↩︎
-
https://www.cncf.io/blog/2020/06/01/5g-rollout-how-kubernetes-and-edge-computing-is-making-5g-a-reality/ ↩︎
-
https://scs.community/about/ therein https://scs.community/assets/images/201001-SCS-4a.png ↩︎
-
Kubernetes adoption, security, and market trends report 2021. ↩︎
-
Docker Hub Container Image Library | App Containerization ↩︎
-
Private vs. Public Container Registries: Pros, Cons and Best Practices - The New Stack ↩︎
-
Over 30% of Official Images in Docker Hub Contain High Priority Security Vulnerabilities ↩︎
-
OPERATION RED KANGAROO: INDUSTRY'S FIRST DYNAMIC ANALYSIS OF 4M PUBLIC DOCKER CONTAINER IMAGES, Half of 4 Million Public Docker Hub Images Found to Have Critical Vulnerabilities ↩︎
-
Container Health Index grades as used inside the Red Hat Container Catalog ↩︎
-
Usage Statistics and Market Share of Linux for Websites, August 2021 ↩︎
-
Alpine - Official Image Independent Comparison A Comparison of Linux Container Images, Guide Alpine Linux - Making Tiny Containers - Complete Intro to Containers ↩︎
-
Bits relating to Alpine security initiatives in August - Ariadne's Space ↩︎
-
Reproducible Builds - a set of software development practices that create an independently-verifiable path from source to binary code, already supported by the Prototype Fund Reproducible Builds in reality, including Alpine ↩︎
-
The author supports administrators in the secure installation and operation of clusters and security auditors in the assessment of security. The content of the workshops and trainings is available under an open source license thomasfricke/training-kubernetes-security ↩︎
-
aquasecurity/kube-bench: Checks whether Kubernetes is deployed according to security best practices as defined in the CIS Kubernetes Benchmark, Blog Kube-Bench: An Open Source Tool for Running Kubernetes CIS Benchmark Tests ↩︎
-
Critical infrastructure customers (transport and healthcare) ↩︎
-
Advanced Persistence Threats - The Future of Kubernetes Attacks, Video: Advanced Persistence Threats: The Future of Kubernetes Attacks - Ian Coldwater & Brad Geesaman ↩︎
-
Training Kubernetes Security: ClusterAdminOpenShift.ipynb ↩︎
-
Deploy ECK in your Kubernetes cluster | Elastic Cloud on Kubernetes \[master\] the author pointed out the problem to Elastic, no response ↩︎
-
Node.JS JavaScript Security | JavaScript Vulnerabilities only ↩︎
-
Author's Kubernetes Security Article Series, Part 1: Concepts Inherited from Linux ↩︎
-
AdmissionController: Using Admission Controllers, Successor to PodSecurityPolicies PodSecurityPolicy Deprecation: Past, Present, and Future ↩︎
-
Network Policies, e.g. Project Calico ↩︎
-
Service mesh, e.g. Istio The Istio service mesh ↩︎
-
https://github.com/thomasfricke/training-kubernetes-security/blob/main/IstioHack.ipynb ↩︎
-
https://de.wikipedia.org/wiki/Seitenkanalattacke#Gemeinsame_Speichernutzung ↩︎
-
Google, private communication ↩︎
-
Red Hat: Determining whether an application has poor cache performance, Trendmicro.com detecting meltdown and spectre ... ↩︎
-
Survey of CPU Cache-Based Side-Channel Attacks: Systematic Analysis, Security Models, and Countermeasures ↩︎
-
private communication with Kurt Garloff ↩︎
-
https://www.cvedetails.com/product/383/Openssl-Openssl.html?vendor_id=217 ↩︎
-
BSI Cryptographic Methods: Recommendations and Key Lengths, Version 2021-01 ↩︎
-
Blockchains implement Distributed consensus to prevent attacks like the Byzantine Generals problem Byzantine error - Wikipedia. In all security-related areas, there is a strong, centralized trust authority due to regulatory requirements. Distrinute consensus is not needed. For this reason hash chains are perfectly sufficient
https://en.wikipedia.org/w/index.php?title=Hash_chain#Hash_chain_vs._blockchain.
The term blockchain has become hype with the advent of cryptocurrencies and is now being softened even in scientific circles and used for hash chains, for "marketing reasons" (private communication, Gesellschaft für Informatik, Fraunhofer) ↩︎
-
"When quantum computing comes, Bitcoin will also be vulnerable". ↩︎
-
Lecture: The year in post-quantum crypto | Friday | Schedule 35th Chaos Communication Congress ↩︎
-
Lecture: (Post-Quantum) Isogeny Cryptography | Friday | Schedule 36th Chaos Communication Congress ↩︎
-
Code Intelligence: Effortless DevSecOps with Modern Fuzz Testing ↩︎
-
implemented by the author with the DevOps team in 2011 at Immobilienscout24, among others, without security checks ↩︎
-
Made-up word from development and operations DevOps - Wikipedia ↩︎
-
DoD Enterprise DevSecOps Strategy Guide, part of DevSecOps - DoD Cyber Exchange, the author dissociates from any military use of FOSS software. ↩︎
-
Sec moves to front, left on diagrams DevOps tech: Shifting left on security ↩︎
-
In the original: "Tailor the organization's operational culture and technical processes to support the new way of developing, running, and supporting applications made possible by containers.", https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-190.pdf ↩︎
-
A Few Billion Lines of Code Later: Using Static Analysis to Find Bugs in the Real World | February 2010 | Communications of the ACM ↩︎
-
Telephone interview with Werner Koch ↩︎
-
SolarWinds: NSA & Co. urge to patch with vulnerability report ↩︎
-
Jitsi: Free Video Conferencing Software for Web & Mobile, BigBlueButton | Open Source Virtual Classroom Software ↩︎
-
SONiC: The networking switch software that powers the Microsoft Global Cloud ↩︎
-
Open Compute Project, Open Infrastructure Foundation (OpenInfra Foundation): Open Source Infrastructure Foundation - Open Infrastructure Foundation (OpenInfra Foundation) ↩︎
-
Most secure Android smartphone NitroPhone released, manufacturer product page NitroPhone 1 | www.nitrokey.com ↩︎
-
Call for Funding K-9 Mail is looking for funding k9mail.app, Cketti Imprint ↩︎
-
private communication with Cketti ↩︎
-
Open Collective - Make your community sustainable. Collect and spend money transparently. ↩︎
-
personal communication with Ariadne Conill, Alpine Linux ↩︎
-
IoT + edge processing is making sci-fi a reality for energy management ↩︎
-
personal communication ↩︎
-
analog sigstore, see above. ↩︎
-
Automated Certificate Management Environment, analogous to a local instance of Let's Encrypt ↩︎
-
Security Chaos Engineering: A new paradigm for cybersecurity ↩︎
-
the author is financially involved in startup that is developing a product in this area, (PDF) Chaos Engineering for Cloud-Native Security, Continuous Auditing & Threat Detection in Multi-Cloud Infrastructure | Request PDF, (PDF) CloudStrike: Chaos Engineering for Security and Resiliency in Cloud Infrastructure ↩︎
-
From
"Please," he pleaded, "stop putting a major or lieutenant colonel (despite their dedication, exceptional attitude, and culture) in charge of ICAM, Zero Trust, or Cloud for 1 to 4 million users when they have no experience in this area - we are building a critical infrastructure that will fail."
The former chief software officer continued:
We wouldn't put a pilot in the cockpit without extensive flight training; why would we expect someone with no IT experience to be anywhere near successful? They don't know what to do or what to prioritize, leading to endless risk mitigation efforts and a dilution of focus. IT is a highly skilled and trained job, so you should staff it that way. ↩︎
-
Neutrality deficit of the BSI Statement Manuel Atug of the independent AG KRITIS on the IT Security Act 2.0 ↩︎
-
Controversial company in Israel: BKA bought spy software from NSO | tagesschau.de, Warning systems in Germany: Germany warns - but unfortunately wrong, IT Security Act 2.0: If Telekom should hack into your computer, Little applause for the planned IT Security Act 2.0, Open letter: For a real cybersecurity strategy without new surveillance measures. ↩︎
-
The Internet Bug Bounty | Rewarding friendly hackers who contribute to a more secure internet ↩︎
-
The problem with bug bounty programs is that they are quite buggy ↩︎