Kubernetes Security
The training has been given at lot of times for different companies. As the handson lessons are complex, the lessons are given as Jupyter Notebooks. All the notebooks are available at Github and have aquired some contributions and stars.
This training is very intense and not adequate for beginners!
Intended audience
Developers, Operations, DevOps, Auditors, Software Architects, Security Architects, CISOs and everybody who wants to deep dive into Kubernetes security.
Prerequesites
Experiences in your field and a very good knowledge of Linux and a good practical understanding of Kubernetes. You need the knowledge of the Introduction into Kubernetes. It is recommended to have at least six months of practical experience.
The handson less are done on the command line interface.
Learnings
You will get the deep insights into Kubernetes security and will be able to handle practical security questions on your own. This includes tools and strategies to build, secure and check your clusters.
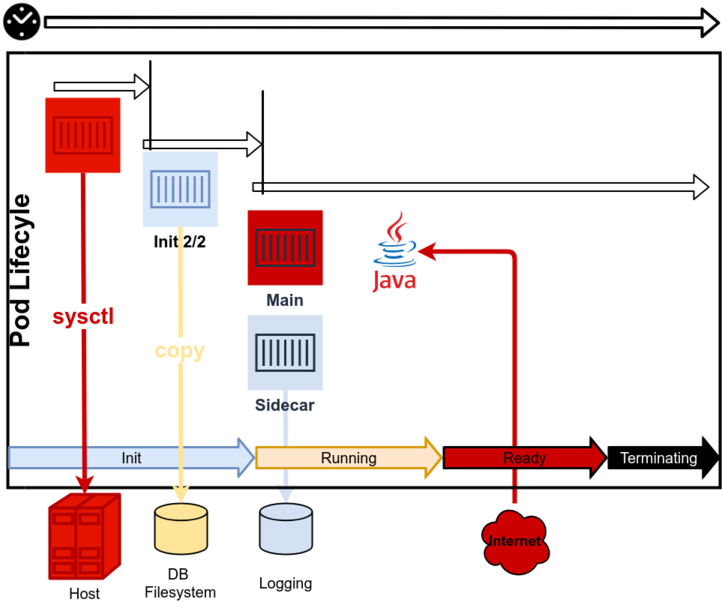
Day One: Introduction
The first day repeats the knowledge of Kubernetes under a security point of view. Secure architectures are discussed with separation of concerns in mind.
- installation of Minikube with the Jupyter notebook environment
- repetiton of the basics
- what is running in my cluster?
- the Linux heritage: Linux Namespaces, Capabilities, SecComp, Selinux and Apparmor
- containers and virtualization
- container runtimes: beyond Docker
- pods, daemonsets, statefulsets and other workloads
- the most common errors
- architectural aspects
- container patterns, designing containers with security in mind
- secure architecture: does an application need privileges
- databases in Kubernetes
- access to the Host Filesystem
- container images
- SecDevOps in secure environments
- filtering
Day Two: networks
The second day focuses on networks and service meshs. How to connect an application securely with the internet. What about service meshs? Do we need them and if yes how to configure them securely.
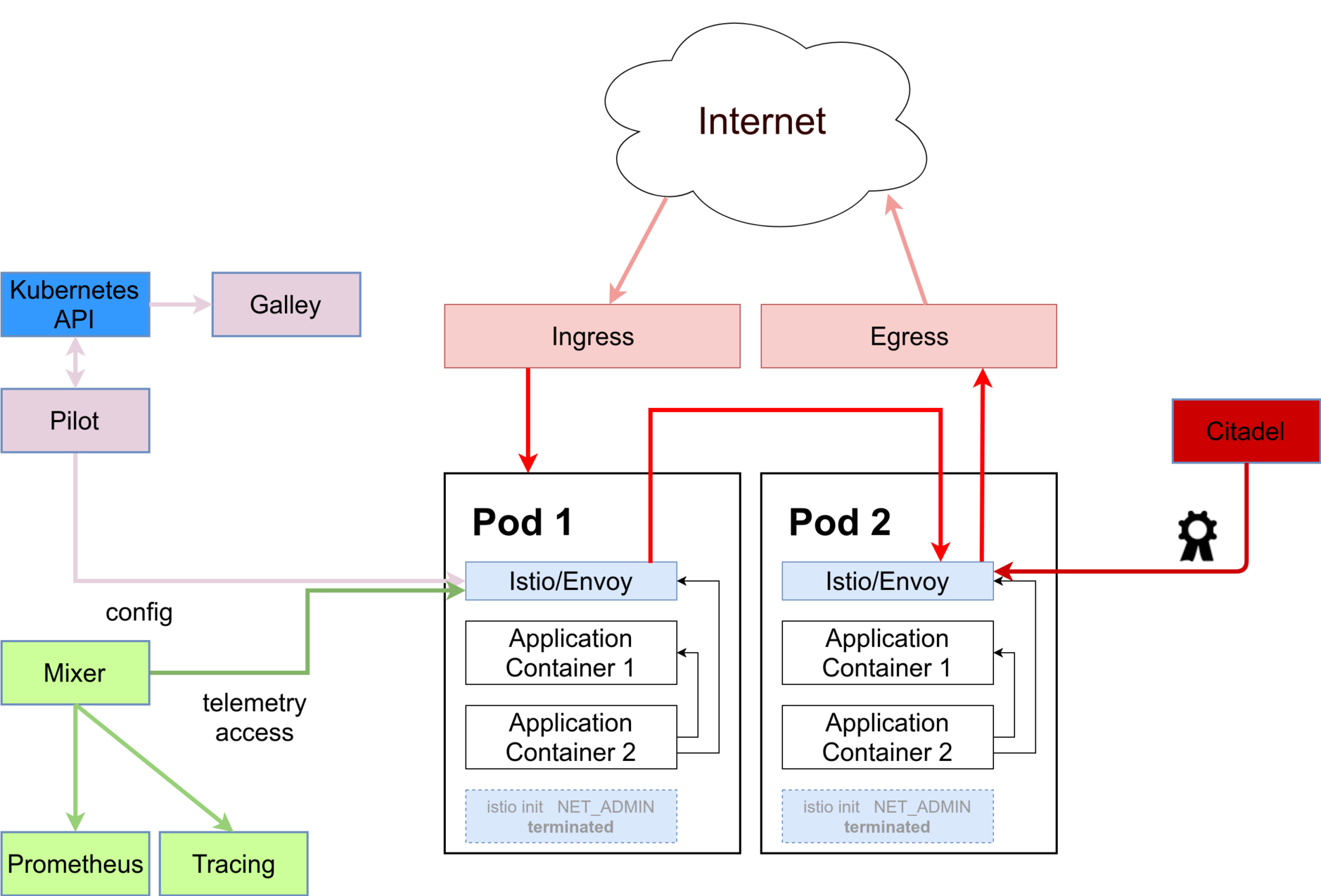
- services
- ingress as an additional network layer
- transport layer security and secrets
- NetworkPolicies
- distributed firewalls
- when do you need service meshs?
Day Three: Hardening Kubernetes
The third day focuses on securing applications. Understanding the built in features allow to create a highly secure environment with security in depth in mind.
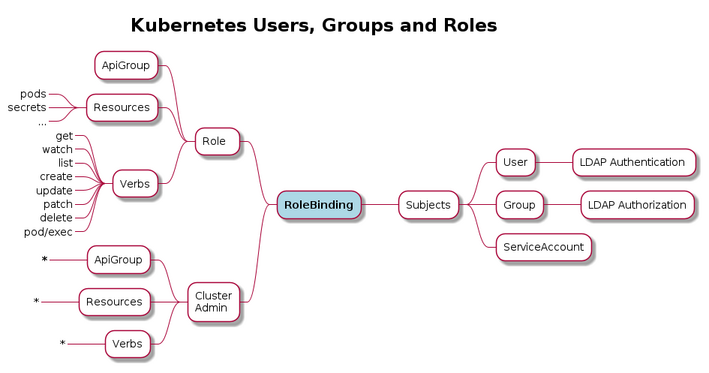
- PodSecurityPolicies
- Admission Controller, Open Policy Agent
- Users, Roles und RBAC (Role Based Access Control)
- Audit Logs
- What is allowed to a Pod?
- distributions
- cloud vendors
- On Premises
- criteria for selecting vendors